The year 2021 was eventful in regards to digital hazards for people and companies, and banks were no exception. Throughout the previous year, we have actually seen cybercriminals continue to actively target our users with tools and methods that emerged due to the pandemic. Flaws in the shift to remote/hybrid work continue to posture a substantial hazard to companies. Financial concerns triggered by the pandemic have actually just exacerbated the issue. Driven by hardship and joblessness, cybercriminals magnified their harmful activity versus bank consumers and bank facilities.
Well-known monetary dangers stay popular. SpyEye, established in 2009 and referred to as a “bank Trojan with a type getting ability”, rose from the 8th most typical banking malware tool with a 3.4% share in 2020 to the 2nd most typical in 2021 with 12.2%. Emotet (9.3%), explained by Europol as “the world’s most hazardous malware”, went through a drop of 5 portion points in between 2020 and 2021. This is connected to the truth that police all over the world collaborated to block the botnet’s facilities at the start of 2021, so its activities were interrupted for a minimum of part of that year.
While 2021 did see a boost in hazards to banks on an international scale, it likewise saw PC and mobile malware advance the down pattern formerly seen in 2020. The mass modification in cybercriminals’ techniques and goals seen in 2020 continued in 2021. Cybercriminals have actually discovered methods to gain from the modifications brought by the pandemic, adjusting their approaches and objectives to make the most of the shifts to teleworking and online shopping. This report intends to provide extensive insights into the monetary cyberthreat landscape in 2021.
The research study in this report is an extension of our previous yearly monetary danger reports ( 2018 , 2019 and 2020 ), offering an introduction of the current patterns and essential occasions throughout the danger landscape. We take a look at phishing hazards frequently experienced by business and users in addition to the occurrence of numerous Windows and Android-based monetary malware.
.Method.
For the functions of this report, “monetary malware” describes destructive software application targeting entities within the monetary services sector, consisting of electronic banking, payment systems, e-money services, online shops and cryptocurrency services. The term is likewise utilized to explain malware looking for access to monetary companies’ IT facilities.
Besides monetary malware, we examined phishing activities, significantly the style and circulation of economically themed websites and e-mails planned to impersonate popular genuine websites and companies in order to trick potential victims into supplying their personal info to be made use of by the cyberattackers.
To analyze the monetary danger landscape, we have actually evaluated the harmful activities on gadgets owned by people running Kaspersky security items, which they offered to offer to us through Kaspersky Security Network . Maliicious activities on gadgets with Kaspersky items were evaluated in addition to business user stats, which were likewise gathered from consumers who consented to share information from their business security options. All stats from Kaspersky Security Network are anonymized.
Data from 2021 was compared to information from 2020 to evaluate year-on-year patterns in malware advancement. For the sake of more insight into evolutionary patterns in monetary malware, periodic referrals to preceding years are likewise consisted of.
.Secret findings.
Phishing:
.In 2021, 8.2% of users were struck by phishing.E-commerce-related phishing continued to surpass banking-related phishing, as it carried out in 2020, comprising 17.6% of all phishing plans in 2021, compared to the 11.1% share for banking.PayPal users kept their position as the most regularly targeted payment system users, with phishing pages imitating this payment system accounting for 37.8% of such attacks in 2021. Visa, previously a long time leader in the classification, kept its 4th location with a 9.4% share.
PC malware:
.In 2021, the variety of users assaulted by banking Trojans continued to decrease from 625,364 in 2020 to 405,985 in 2021 –– a 35% drop.The nations with the biggest varieties of targeted users in 2021 were Turkmenistan, Afghanistan and Tajikistan.Zbot (20.5%) stayed the most widespread banking malware, followed by SpyEye (12.2%), which saw a noteworthy dive in existence, and CliptoShuffler (10.2%).Business risks from banking malware grew by nearly 2 portion indicate 37.8%, with the staying 62.2% representing customer banking malware attacks.
Mobile malware:
.In 2021, the variety of Android users assaulted by banking malware saw another sheer drop, with numbers falling from 294,158 in 2020 to 147,316 in 2021 –– a 50% drop.Amongst nations and areas worldwide, we observed the greatest portion of Android users targeted by banking malware in Japan, Spain and Turkey. Turkey changed Taiwan in the leading 3, with the latter totally falling off the leading 10 list.Financial Phishing.
Phishing is among the most common kinds of cybercrime due to very little effort needed and the reality that it truly works. It’s typically developed around a naturally basic plan: utilizing thoroughly crafted e-mails or notices that simulate messages from banks, federal government companies, home entertainment platforms –– truly any service –– cybercriminals can deceive users into following a link to a deceptive site and quiting their payment or individual information and even downloading harmful programs.
In 2021, Kaspersky anti-phishing innovations discovered over 250 million efforts to follow a phishing link on user computer systems, with 8.2% of users experiencing an attack. As lots of as 41.8% of those attacks were connected to monetary phishing.
Percentage of monetary phishing attacks (of the total phishing attacks) discovered by Kaspersky, 2016 –– 2021 ( download )
In this case, “monetary phishing” refers not just to banking particular phishing however likewise payment systems and e-shops. Payment system phishing consists of pages impersonating widely known payment brand names, such as PayPal, MasterCard, American Express, Visa and others. E-shops describe online shops and auction websites like Amazon, the Apple Store, Steam, eBay and so on
In 2021, phishing cases identified by Kaspersky revealed that e-shop phishing was the most typical, representing 17.6% of all phishing and over 40% of monetary phishing. We associate the considerable size of these figures to the effect of the pandemic on users’ innovation practices, with numerous beginning to do more shopping online, increasing the prospective supply of targets for cybercriminals.
Payment systems were the target of about one-third of all monetary phishing and banks comprised the rest at 26.6%, representing 11.1% of all phishing cases.
Distribution of monetary phishing cases by enter 2021 ( download )
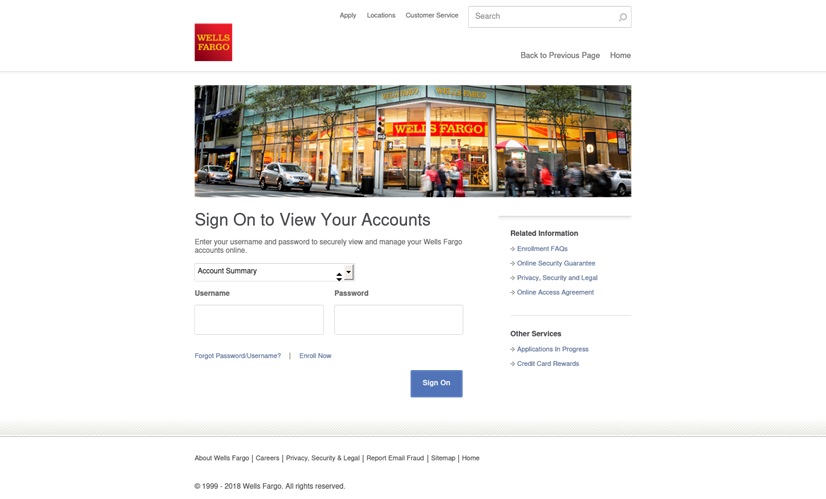
The bank-related phishing example listed below displays the resemblance of phony pages to the genuine business they are impersonating. Phishers utilize the bank’s logo design and an image of its workplace. Victims would error it for a genuine bank page and unwittingly relay all info required to access their accounts.
A phishing login and account confirmation page mimicing a U.S. monetary services business, Wells Fargo
Payment system brand names most regularly utilized in monetary phishing plans, 2021 ( download )
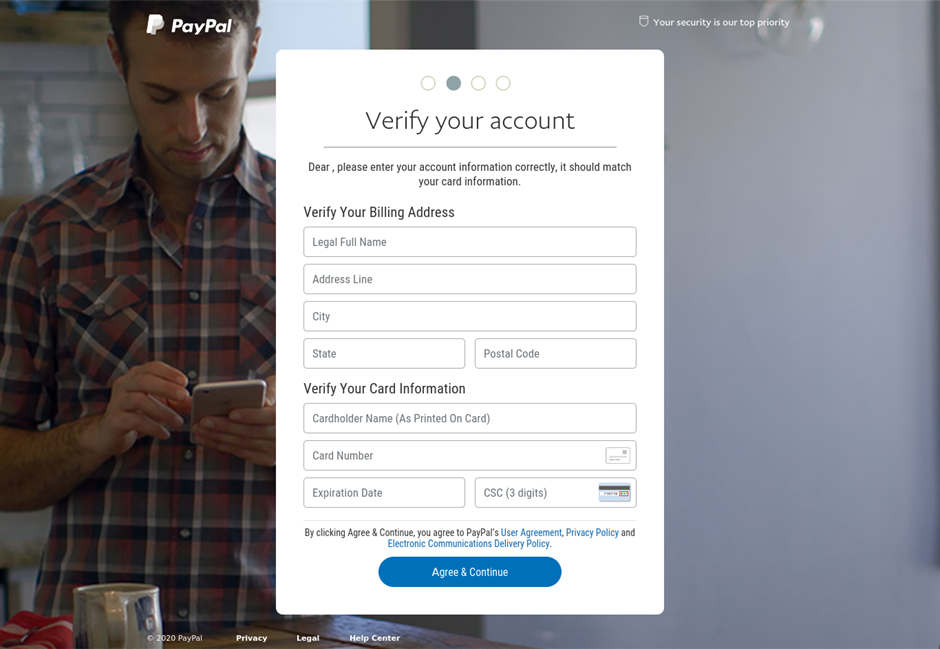
As the chart above programs, PayPal was without a doubt the most typically utilized payment system in phishing attacks, comprising 37.8% in 2021.
This example of a phishing page targeted at PayPal users straight asks potential victims to include their payment information
Meanwhile, Mastercard held second-place in the assaulted payment systems ranking at 12.2%. American Express phishing rip-offs likewise have actually held constant for many years with 10% in 2021.
E-shop brand names most often utilized in monetary phishing plans, 2021 ( download )
Throughout the previous year, fraudsters thoroughly targeted users of different retail platforms. In 2021, Apple was the most pre-owned brand name for phishing plans at 48.78%. Amazon held 2nd location with 21.48%. EBay visibly took just 5.32% in 2021. Alibaba, a Chinese international tech business, is likewise in the leading 4 assaulted online shops of 2021. The business’s users were the target of 4.14% of phishing plans.
An example of a phishing login page targeting Amazon consumers worldwide
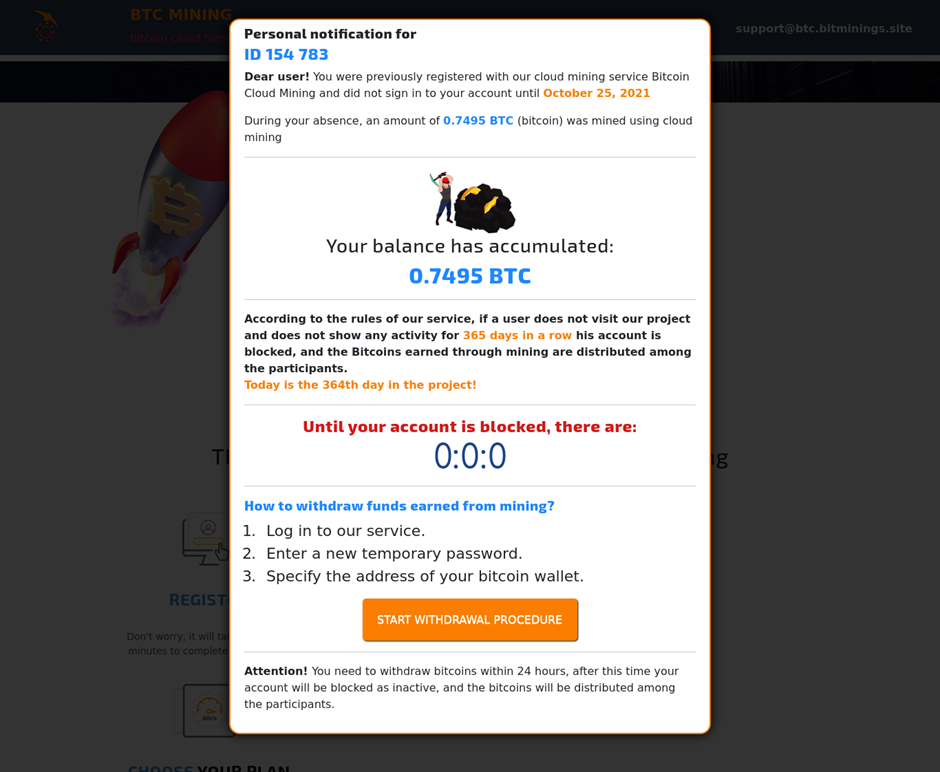
An obvious advancement was the prominence of cryptocurrency-related phishing frauds. In 2021, there were over 460,000 crypto-related phishing efforts. This might possibly be described by the growing pattern and legitimization of Cryptocurrencies and nfts, in addition to cryptocurrency rates, which skyrocketed at the end of 2020 and remained high throughout 2021.
An example of a phishing page targeting financiers and debtors of numerous cryptocurrencies
Cryptocurrency-related phishing plans are most likely to grow as this more recent digital payment system continues to get appeal, since with increased uptake comes more prospective victims to cybercriminal activities. Cryptocurrency costs are not to be undervalued: if Bitcoin drops in 2022, the total interest in cryptocurrency might likewise drop. In February 2022, we observe it beginning growing once again.
.Banking malware for PC.
This research study analyses the banking malware utilized to take qualifications required to gain access to victims’ electronic banking or payment systems accounts and to obstruct one-time passwords for two-factor authentication.
Our findings revealed that in 2021, the variety of users assaulted by banking malware continued to decrease, going from 625,364 in 2020 to 405,985 in 2021 –– a 35% drop. This follows a progressively downhill pattern, with this figure dropping 20% in between 2019 and 2020, and a near 13% in between 2018 and 2019.
This pattern is credited to the progressively targeted nature of attacks, as cybercriminals pivot to focusing on big organization targets. People and little companies stay a big percentage of those preyed on by cybercriminal groups like Zbot, SpyEye, CliptoShuffler and Emotet, amongst others.
Dynamic modification in the variety of distinct users assaulted by banking malware in 2019 –– 2021 ( download )
The primary stars amongst banking malware.
Every year, we spot several households of banking malware –– groups of applications with comparable attack strategies and the exact same code base. The lifecycle of these malware households differs, some end up being outdated and others just broaden.
TOP 10 PC banking malware households, 2021 ( download )
Our tracking of the banking malware households revealed that about half of all impacted users were assaulted just by 4 households. Zbot kept its position as the most popular malware with monetary cybercriminals, comprising one-fifth of all attacks. SpyEye made a significant dive from number 8 on the list to second, going from 3.4% in 2020 to 12.2% in 2021. Gozi and Nuerevt fell out of the leading 10, the previous of which represented one= fifth of all monetary malware attacks in 2018. They were changed by Cridex and Nymaim.
.Location of assaulted users.
For this report, we computed the portion of Kaspersky users in each nation that came across a danger out of the overall variety of Kaspersky users in the nation in order to establish the danger of computer system infection in various nations around the globe. Keep in mind that in previous reports, we utilized a various method. For this factor, numbers for the year 2020 in this area will likewise be various.
TOP 20 nations with the best share of assaulted users exist in the table listed below. Over half of all infection tries happened in these 20 nations.
.Nation *.Share of assaulted users.Turkmenistan.8,3%.Afghanistan.6,4%.Tajikistan.6,4%.Uzbekistan.5,3%.Yemen.3,1%.Paraguay.2,6%.Sudan.2,4%.Kazakhstan.2,1%.Syria.2,1%.Zimbabwe.2%.Lithuania.1,8%.China.1,7%.Venezuela.1,7%.Costa Rica.1,6%.Pakistan.1,5%.Kyrgyzstan.1,5%.Iran.1,4%.Belarus.1,4%.Cameroon.1,3%.Egypt.1,2%.
* Countries with less than 10 000 Kaspersky users are omitted from these stats
Turkmenistan (8.3%) was the most assaulted nation by banking malware for PC. Afghanistan (6.4%) and Tajikistan (6.4%) share 3rd and 2nd location, respectively. Uzbekistan (5.3%), which was the leader in 2020, now landed 4th, losing 3.5 p.p., and Yemen (3.1%) reached the 5th position.
The shares of Paraguay (2.6%) and Sudan (2.4%) grew a little, while Kazakhstan (2.1%) and Syria (2.1%) lost around 1 p.p. and shared ninth and 8th locations. Zimbabwe (2%) complete the TOP 10, and Lithuania (1.8%) included 1 p.p. and reached eleventh position.
.Kinds of users assaulted.
Our research study has actually verified our hypothesis that monetary malware is ending up being progressively business instead of customer focused. In between 2020 and 2021, business users’ share of banking malware targets increased by practically 2 portion points and grew by a visible 13.7 portion points in between 2018 and 2021. In current years, the development of business user share has actually been significantly slower than in the pre-pandemic years, and attacks versus customers still exceed business dangers with the previous making up 62.2% of monetary malware attacks in 2021 and the latter, 37.8%.
PC malware attack circulation by type (business vs customer), 2020–– 2021 ( download )
We associate this to the continuing shift towards a hybrid and remote modes of work. The pandemic saw an increase and fall in the number of limitations, numerous business chose not to come back to the familiar workplace work mode. In some companies, workers had to resort to utilizing house gadgets safeguarded by customer services for working functions. The detection will count as customer targeting if these users get a harmful message both by business and individual e-mail. That implies that cybercriminals might be a lot more thinking about business users than our data reveal.
.Mobile banking malware.
Kaspersky specialists have actually been evaluating Android banking malware for several years and have actually observed an intriguing high down pattern.
In 2019, the variety of Android users assaulted by banking malware dropped from 1.8 million in 2018 to a little over 675,000. In 2020, the figure dropped an extra 55% to 294,158. This year we saw a comparable drop of practically 50%, making the overall variety of Android users assaulted with banking malware in 2021 147,316.
Number of Android users assaulted by banking malware by month, 2021 ( download )
To comprehend these patterns, we evaluated the effect and modifications of the most widespread mobile malware.
The year 2021 saw Agent supplant Asacub as the number-one mobile malware, representing 26.9% of attacks. Asacub (18.8%) dropped from its primary positioning in 2019 and 2020 to 3rd in 2021, dropping 6.8% portion points considering that 2020. Svpeng (21.4%), which looks for administrator rights on contaminated gadgets, grew by practically 9 portion points in between 2020 and 2021, hence recovering its position in the TOP 3, and going beyond Asacub.
In 2020, Rotexy (1.6%), which has abilities of both a banking Trojan and a ransomware locker, was the 3rd most typical kind of Android banking malware with a 17.9% share. In 2021, Rotexy dropped by 16.3 portion points to tenth location.
TOP 10 Android banking malware households, 2021 ( download )
Geography of assaulted users.
TOP 10 nations and areas by portion of Android users targeted by banking malware in 2020.
.Country/region.Share of users *.Japan.2,83%.Taiwan.0,87%.Spain.0,77%.Italy.0,71%.Turkey.0,60%.Korea.0,34%.Russian Federation.0,25%.Tajikistan.0,21%.Poland.0,17%.Australia.0,15%.
* Number of users experiencing mobile banking malware as a portion of the overall variety of users of Kaspersky mobile services in the nation or area
TOP 10 nations and areas by portion of Android users targeted by banking malware in 2021.
.Country/region.Share of users *.Japan.2,18%.Spain.1,55%.Turkey.0,71%.France.0,57%.Australia.0,48%.Germany.0,46%.Norway.0,31%.Italy.0,29%.Croatia.0,28%.Austria.0,28%.
* Number of users coming across mobile banking malware as a portion of the overall variety of users of Kaspersky mobile options in the nation or area
Interestingly, Japan (2.18%), which did not make the leading 10 in 2019, was when again the top nation in 2021 after increasing to the leading position in 2020. Russia went from remaining in the leading position in 2019, to seventh in 2020, to totally falling out of the leading 10 for 2021. Taiwan, the number-two area in 2020, likewise did not make the leading 10 in 2021. Korea, Tajikistan and Poland likewise lost their positions. These areas and nations were changed by 5 beginners: France (0.57%), Germany (0.46%), Norway (0.31%), Croatia (0.28%) and Austria (0.28%).
.Conclusion.As soon as again revealed a decrease in the number of users impacted by mobile and PC malware, #ppppp> The year 2021. This looks comforting, though the dangers of infection are far from being gone. We have actually observed another little boost in the share of malware attacks versus business users versus customers. If the users working on individual gadgets are taken into account, the pattern of banking Trojans targeting business users continued; this is of issue particularly.
Our research study likewise discovers that phishing fraudsters’ increased concentrate on e-shops over banks, which started in 2020, is here to remain for the time being as the pandemic impacts on customer habits continue. These results consist of increased online shopping over conventional physical, a result that lots of economic experts forecast will last longer than the pandemic. Cryptocurrency users will be alert, too, for while Bitcoin rates stay high, this is a honey pie for cybercriminals.
For defense versus monetary dangers, Kaspersky suggests that users:
.Set up just applications acquired from trustworthy sources.Avoid authorizing approvals or rights asked for by applications without very first guaranteeing they match the application’s function set.Never ever open files or links consisted of in suspicious-looking and unanticipated messages.Set up a relied on security option, such as Kaspersky Security Cloud , which safeguards you and your digital facilities from a large range of monetary cyberthreats.
To secure your service from monetary malware, Kaspersky security professionals suggest:
.Offering cybersecurity awareness training , specifically for workers accountable for accounting, that consists of guidelines on how to find phishing pages.Improving the digital literacy of personnel.Allowing a Default Deny policy for important user profiles, especially those in monetary departments, which makes sure that just genuine web resources can be accessed.Setting up the current updates and spots for all software application utilized.
Read more: securelist.com