Founded in 2002, Jamf is an identified tech leader that develops IT software application that handles Apple gadgets. More than 50,000 organisations count on Jamf to handle over 20 million gadgets, consisting of 24 of the 25 most important brand names throughout markets all over the world. In addition to Apple, the business has actually likewise broadened its offerings to support Windows and Android.
In July 2021, the business obtained Wandera , a leader in Zero Trust Cloud Security and Access. With the acquisition, Jamf is distinctively placed to assist IT and security groups with confidence safeguard gadgets, information, and applications while extending the designated Apple experience through the most scalable and robust Apple Enterprise Management platform in the market.
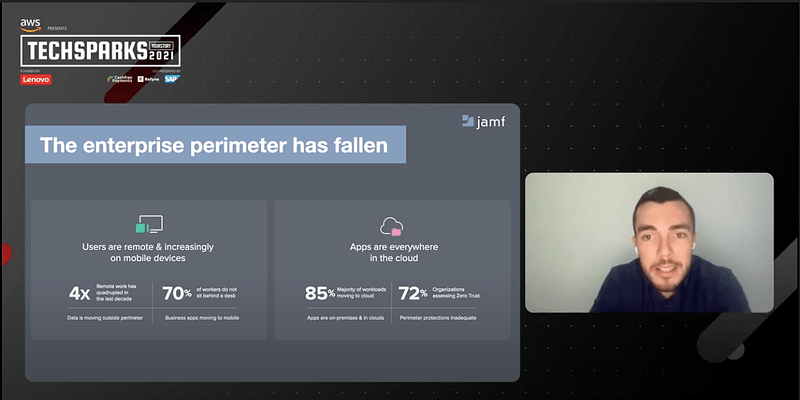
At YourStory’’ s TechSparks 2021, India ’ s most prominent startup-tech conference, Adam Boynton, Regional Sales Manager, Wandera, a Jamf business, highlighted why there is a requirement for a Zero Trust Network Access design and how it can provide worth for business.
More than half of all web traffic is related to a mobile phone. And with many organisations requiring to hybrid work, mobile is now part of a regular workday for many staff members.
Business applications are following a comparable course, transitioning out of the information centre into the cloud. Today, more than 85 percent of organization applications are being hosted in cloud platforms, which increases service dexterity and makes staff members more efficient than ever.
.READ. How digital adoption and decluttering innovation can assist start-ups endure..The essential difficulties with VPNs
How digital adoption and decluttering innovation can assist start-ups endure..The essential difficulties with VPNs
““ The method IT services are provided and taken in has actually essentially altered business security. With considerable advances in cloud computing and mobile innovations, information is no longer constrained to business information centres, which undoubtedly indicates the business border has actually fallen,” ” Adam discussed.
He shared that while generally, virtual personal network (VPN) has actually been the method which services have actually allowed access to their workers, it is now ending up being a tradition service.
A crucial style defect of the VPN is that it is insecure by style.
““ VPN tools normally link users to remote network sectors that house several applications. This indicates any user or an assailant that can get onto the network to access a single application can likewise access whatever else within the network.””
Large VPN releases are likewise complicated to handle, sometimes requiring big devoted groups. The other usually ignored difficulty with VPNs is its influence on efficiency. In addition to slow connection speeds, VPN substantially affects the gadget’’ s battery.
““ VPNs were not created with end-users in mind,” ” Adam shared, going on to describe why a Zero Trust Network Access ends up being the most popular innovation to change a tradition VPN.
Understanding Zero Trust Network Access
Zero Trust Network Access is basically an IT security design that needs rigorous confirmation of every private gadget that tries to gain access to delicate resources on the network, no matter where they lie.
““ The very first concept of Zero Trust Network Access is trust nobody,” ” Adam stated.
Adam likewise described how the identity and authentication of an end-user is a foundation of the design.
““ So, one method to consider Zero Trust Network Access is that it develops and handles individualised boundaries including 2 entities – the user and the application with which they are engaging. Prior to linking to the user, an application and the gadget need to verify and confirm they have approval to gain access to that specific application.” ”
For example, an organisation with several applications that are being preserved by it would utilize Zero Trust Network Access to require user gadgets or work to be authorised independently for each application gain access to.
In addition to the stringent controls on user gain access to, Zero Trust Network Access systems should be device-aware and need guarantees that every gadget is authorised. By rejecting connections for confidential gadgets, the attack surface area is eventually more reduced.
Advanced zero-trust security designs likewise integrate danger evaluation of each gadget, leaving absolutely nothing to opportunity. These, he kept in mind, were a few of the huge aspects that are speeding up the switch.
In truth, Gartner forecasts that by 2023, 60 percent of organizations will phase out their VPN and change them with Zero Trust Network Access.
Why CXOs ought to check out purchasing Zero Trust Network Access Solutions
Addressing IT leaders, Adam stated in addition to modernising an organisation’’ s approach to cybersecurity, increasing organization resiliency, cultivating end-user efficiency, and allowing quicker implementation of brand-new applications, Zero Trust Network Access likewise assists to reduce functional expense.
““ Firstly, the direct expense of utilizing a cloud-based Zero Trust Network Access service is normally half that of a conventional remote gain access to service.””
Adam likewise stressed that a Zero Trust Network Access option is more than simply about security. Unlike other security services, the services enhance the dexterity and versatility of business while likewise reducing expenses. He included that an included benefit to think about is that the real expense of the migration is really little, driven by its cloud-based architecture and a scalable licencing design.
Secondly, Zero Trust Network Access operates in parallel with existing remote gain access to innovations while they’re being phased out. This design enables organisations to really effectively release brand-new applications or important applications by means of Zero Trust Network Access services whilst leaving the bulk linked by means of that tradition service that remains in usage.
Then, as organization applications are updated or transferred to the cloud, they can quickly be moved to Zero Trust Network Access options.
So in contrast to numerous old innovations that operate on applications hosted in the information centre, as SaaS-based options, Zero Trust Network Access options do not need hardware to keep track of, software application to spot upgrade, or rackspace that is leased in an information centre for an existing remote gain access to home appliance, leading to an instant expense decrease.
As a cloud-based service, all functional jobs are carried out by the company who guarantees that the service is kept to enterprise-grade requirements.
Adam shared that since Zero Trust Network Access Solutions reduce the intricacy of the innovation stack, the variety of hours invested throughout the style of implementation will lower considerably. This would have an incremental result and considerable cost savings over numerous years.
Zero Trust Network Access services are really developed to make it possible for the modern-day work environment and its remote workplace, Adam stated.
Watch the video to deep dive into Zero Trust Network Access and the functions of Jamf security portfolio.
To visit to our virtual occasions platform and experience TechSparks 2021 with countless other startup-tech lovers from around the globe, sign up with here . When you share your experience, knowings and preferred minutes from TechSparks 2021, do not forget to tag #TechSparks 2021.
For a line-up of all the action-packed sessions at YourStory’s flagship startup-tech conference, have a look at TechSparks 2021 site .

Edited by Teja Lele Desai
.
Read more: yourstory.com
