In this post, we’ll take a look at 4 Linux distros that assist to keep you confidential on the internet. The Linux os uses a great deal of personal privacy alternatives, and it’s perhaps the very best OS to utilize if security and personal privacy is essential to you.
.The Privacy Problem.
It’s challenging to remain confidential online nowadays. Whether you’re searching the Web and even utilizing programs linked to the Internet, you’re being tracked. Even your os is viewing you.
By running an os like Windows, or a program like VS Code, you’re being tracked through telemetry. The majority of the information that’s gathered about you is utilized to enhance the software application you utilize every day, however if your top priority is to remain confidential, you must be searching for much better alternatives.
Various distros of the Linux os deal includes that improve privacy and personal privacy. Being confidential can have downsides.
Before I go on, a disclaimer of sorts. The goal of this short article is to reveal what’s offered for securing your personal privacy. It’s not planned as a motivation to participate in practices forbidden by your nation’s laws.
.What Does It Mean to Be Anonymous?
Staying confidential can imply various things to various individuals, so let’s clarify this idea prior to carrying on.
To remain confidential online, you require to develop who you’re concealing from, and what tools will allow you to conceal your genuine identity.
You can utilize a danger modeling technique to determine the dangers you may be exposed to. To put it just, the U.S. National Institute of Standards and Technology (NIST) has 4 actions:
.define the system and determine and information of interest.determine and choose the attack vectors to be consisted of in the design.identify the security manages for alleviating the attack vectors.examine the hazard design.
If you need to know more about risk modeling, follow the NIST draft , that includes in-depth info about this procedure.
For example, a reporter might wish to remain confidential while sharing their ideas on the internet. This would eliminate the worry of discrimination or retaliation. Basically, they do not desire individuals to understand who they are, so they understand who they should conceal from.
Once you understand who you wish to remain confidential from, it’s time to utilize tools like Tor or the anonymity-focused Linux distros revealed next.
Of course, privacy has numerous benefits, however here are the primary ones:
.liberty of speech: you can share your ideas without the worry of being evaluated.Less tracking: it’s harder to track what you’re doing online.Individual security: nobody understands your genuine identity.Information security: your information is valuable, and remaining confidential makes it more difficult to take it.Different Methods for Using the Following Distros.
In basic, Linux-based os are more privacy-oriented and safe and secure than exclusive ones. Taking this into account, it’s essential to understand how the following distros work, and how they’ll assist you remain confidential.
.Utilizing Virtual Machines.
Virtual makers (VMs) are environments that work as a virtual computer system that operates on top of your physical computer system.
VMs are separated from the remainder of the system, and they can be utilized to run nearly any os, so they support the following Linux distros.
The most popular software application for running VMs is VirtualBox , which is an open-source hypervisor developed by Oracle. It operates in Windows, Linux, and macOS, and is simple to establish.
From a regular user viewpoint, the primary benefit of utilizing a VM is that you can run it in addition to your host running system, which indicates you can utilize both at the very same time.
.Utilizing a Live Boot USB.
A live USB runs an os without installing it on your computer system. When you utilize it to set up a Linux distro, a live USB lets you leap into a live environment. A fine example of this is the Parrot OS live environment, envisioned listed below.

The primary benefit of this approach is that you do not require to set up anything, so you can run the live USB on your computer system, utilize the Linux distro, disconnect the USB, and continue utilizing your daily-driver OS.
Take an appearance at Qubes for an overall VM-based os.
.Setting Up on Bare Metal.
If you wish to remain confidential, setting up a Linux distro as the primary OS on your system isn’t the very best alternative, because you’ll be utilizing your computer system through numerous sessions.
Each time you utilize your computer system, you leave traces of info about the sites you’ve gone to, files you opened, and even the Wi-Fi network you utilized.
That’s why utilizing a live boot USB, or a VM, is normally more safe.
Once you’re finished with the live environment, shut it down and all the information will disappear. With VMs, you can erase them as soon as the task is done.
.Prior to Jumping In, What’s Tor?
Tor —– The Onion Router —– is an open-source task that conceals your IP address when searching the Internet. It reroutes your web demand to an around the world overlay network with over 6 thousand relays.
When you utilize Tor, you’re routing all of your web traffic through 3 makers picked from countless volunteer computer systems from various individuals and companies.
The very first relay understands who are you, however not the next relay you’re going to link to. The 3rd relay just understands where you’re going (an external server, such as a websites) however not your initial IP address.
All of this happens in an encrypted environment, which’s why it’s so essential to prevent insecure pages —– those without HTTPS.
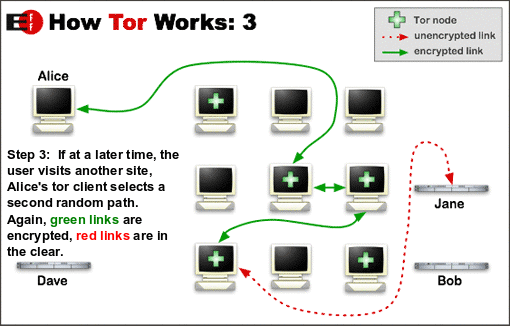
This procedure makes it practically difficult for anybody (sites, web suppliers, and so on) to understand your IP address.
.When utilizing Tor, what not to do.
Tor lets you conceal your IP address, however it spoils if you do not utilize it effectively. Here are a number of things you should not do when utilizing Tor:
.verify utilizing your cellular phone.usage individual social accounts in Tor (Twitter, Facebook, Gmail).share individual info.utilize an old Tor variation.usage Google search; DuckDuckGo does not gather user information.search any non-HTPPS (unencrypted) websites.
Once you’ve internalized these suggestions, you can utilize a faster way produced the typical user, the Tor internet browser package.
Nowadays, you can download the Tor Browser which is an internet browser that works on top of Tor in all significant os. If you desire, you can likewise assemble and download Tor source code .
But utilizing Tor has some disadvantages. The most crucial one is that it restricts your web speed. This happens since you’re routing your traffic through the Tor network, which indicates each web demand you do needs to go by several computer systems.
Another drawback is that some sites like Netflix, Bank websites, and so on, are obstructed by Tor. If you utilize Tor frequently, you’ll require to fill in CAPTCHA kinds in many pages you check out .
Of course, this is a little rate to spend for security and privacy.
.Tails.
Tails is a confidential Linux circulation based upon Debian. It’s a quick and light-weight os which utilizes Gnome as its default desktop environment.
.When you leave, #ppppp> It begins from a tidy state and leaves no trace. That’s called ““ amnesia ”, and it’s the magic that makes Tails a protected OS. Since Tails does not compose to disk at any point, you can utilize somebody else’s computer system safely.
Another remarkable feature of Tails is that it utilizes the Tor relay as the only method to access the Internet. That indicates that all the networking programs you utilize (programs that require to link to the Internet) should reroute their traffic through a Tor network.
So even if you’re utilizing an easy app like Thunderbird, all the details it recovers or sends out from the Internet need to travel through Tor.
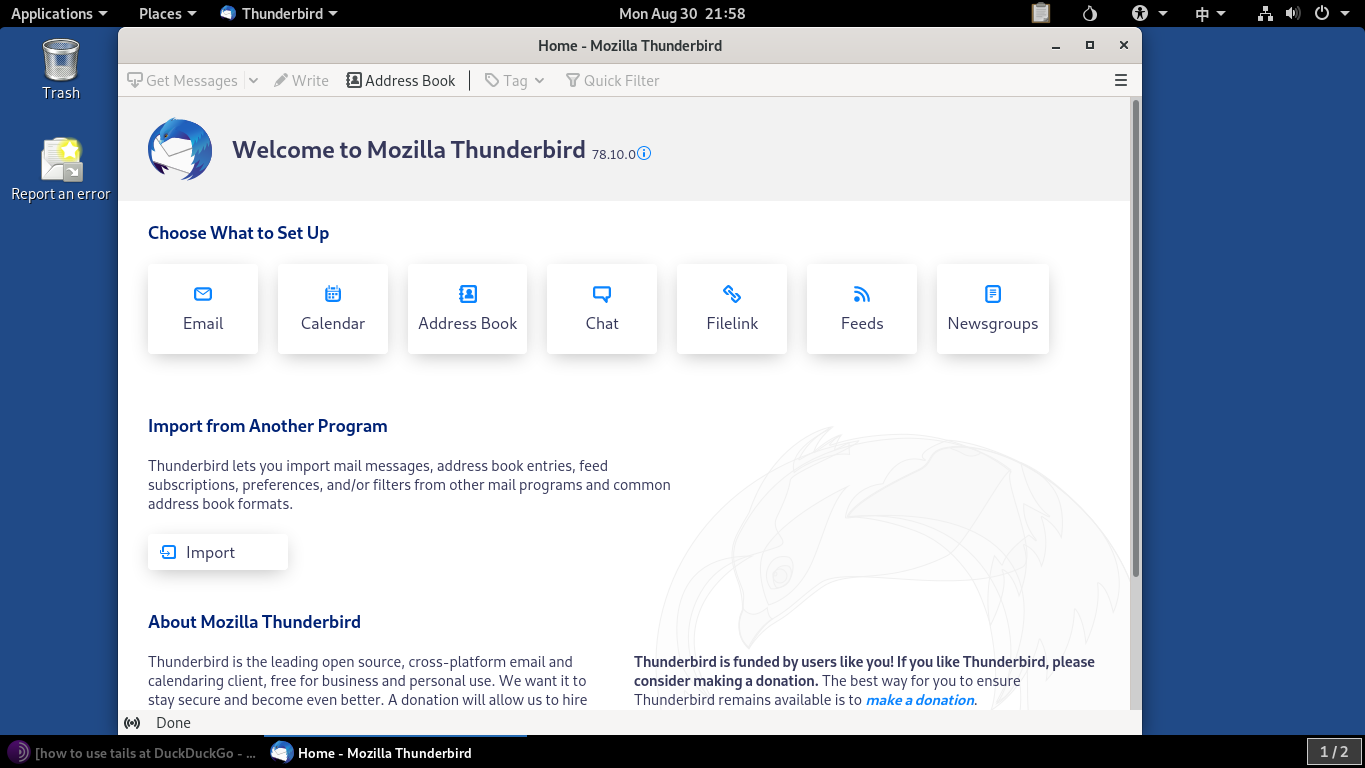
By default, Tails has actually set up the following apps:
Thunderbird Tor Browser , with Ublock Origin, and DuckDuckGo as the default online search engine. Libre Office .visual modifying apps like GIMP and Inkscape.
After utilizing it for a while, it seems like a strong yet light-weight os, so you might run it on old computer systems. (It’s based upon Debian 10)
Also, I discovered this distro can be found in useful when utilizing a buddies’ computer system, so you can keep both users’ information safe.
.Tails Features.Tor relay for whatever.Tails’ storage isn’t consistent, so there’s no other way to track you after you log out. You can make it possible for an encrypted/persistent storage in case you require to set up some other program or conserve some extra settings.It links to the hardware of the computer system however does not communicate with hard disk drive.You can utilize it on virus-infected gadgets without any danger.It consists of common-use apps, in addition to file encryption and privacy-focused software application .It permits you to set up any plan readily available in main Debian repositories.
You can access a more breakdown of functions on Tails’ main site .
.Tails download choices.
You’ll require to download Tails’ USB stick variation and install it on an 8Gb USB (or higher).
If you desire other alternatives, Tails provides 2 methods of use: by means of USB stick, and by means of virtualization (for usage inside a VM).
Here are the various setup images:
Note: Running Tails in a VM has 2 issues. Your host OS and hypervisor can monitor what you’re carrying out in Tails, and Tails can leave traces on the hard drive, which is why it alerts you when you’re utilizing it in a VM.
.If you desire to get some degree of convenience (utilizing Tails without rebooting your PC) while losing a little bit of security, #ppppp> It’s up to you.
Continue reading. The 4 Best Linux Distros for Helping You Stay Anonymous .on SitePoint
.
Read more: sitepoint.com
